|
|
Process Commander offers two Types for
sensitive Single Value, Value List
and Value Group properties: Password
and TextEncrypted.
Both types produce encrypted (or hashed) values for the
property value within the PegaRULES database, and both types
offer some degree of security within the user interface.
When choosing which Type value to use, consider these factors:
Password type requires no advanced
configuration or Java skills to set up. Several standard
properties implement this type; for example, the property
Data-Admin-Operator-ID.pyPwdCurrent. Process
Commander applies the one-way MD5 message digest algorithm to
this value, which is never sent to any external system.TextEncrypted type
requires one-time Java coding of encryption Java functions of
your choice to implement a Public API Interface. (A working
sample is provided).Password value is either a string of asterisks
or the hexadecimal hash value, for all users, in all
situations. The Password value is never decrypted. In
contrast, the value of a TextEncrypted property
can appear in clear text or as asterisks, depending on the
runtime outcome of an access when rule
(Rule-Access-When rule type). Thus your
application can make the clear-text value visible to specific
users, or on certain reports, or during specified time
periods.Password properties are initially added to
the clipboard as unencrypted, clear text values. The system
computes the hashed value only as the page is committed to
the PegaRULES database. Thereafter, the hashed value appears
in both the clipboard and the database row.TextEncrypted values are always encrypted on
the clipboard and in server-to-database network
messages.1. Create a Java class that implements the following PublicAPI interface:
com.pega.pegarules.crypto.IPRCipher
Your implementation can start with the working sample, which is based on the Blowfish algorithm:
com.pega.pegarules.crypto.PRCipherSampleBF
![]() However, don't use this
sample directly without modification. Using a custom
implementation provides your enterprise with greater security,
as it makes your site-specific encryption differ from the
sample.
However, don't use this
sample directly without modification. Using a custom
implementation provides your enterprise with greater security,
as it makes your site-specific encryption differ from the
sample.
2. Update the prconfig.xml file (on each node)
to add lines that identify the Java class:
<env
name="crypto/sitecipherclass"
value="cccc" />
<env name="classloader/classpath"
value="dddd" />
where cccc is the class name and dddd identifies the directory containing the class. (You can omit the second line, depending on the class paths of your system.)
3. Redeploy and restart to make the
prconfig.xml changes effective.
4. Create one or more properties that use the
TextEncrypted type. Complete the General tab:
TextEncrypted.pxRequestor page or other
clipboard pages.5. Reference the property normally in other rules.
6. Implement the identical prconfig.xml changes
and Java class on each server node of a cluster. If you attempt
to decrypt a property value but no cipher algorithm is defined
on that node, the system records an exception in the Pega log
similar to the following:
com.pega.pegarules.pub.context.CryptographicException: decrypt: No site-specific cipher algorithm
You can use a TextEncrypted property in
expressions, testing for equality or inequality only. Call the
standard function rule encryptPropertyValue() to
encrypt the comparison value (a constant, a property value, or
computed text value) before the comparison. For example:
@encryptPropertyValue("Virginia") == .myEncryptProperty
.myEncryptProperty != @encryptPropertyValue(.pyLabel)
The access when rule test and automatic encryption (or decryption) occur only as users interact with a form. In all other cases, your application must explicitly call the functions.
![]() Process Commander allows
comparisons other than equality or inequality, but results are
unpredictable.
Process Commander allows
comparisons other than equality or inequality, but results are
unpredictable.
Process Commander does not perform any automatic type
conversions for TextEncrypted properties during
Property-Set operations. As a result, it is rarely useful to
directly assign an encrypted value to another property, or
assign another property value to a TextEncrypted
property.
When a TextEncrypted property is set to a value, the system
encrypts the value unless it is already encrypted. For example,
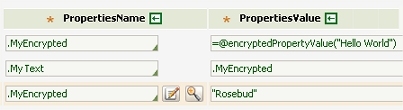
in an activity, a Property-Set method operates on two
properties MyEncrypted (of type TextEncrypted) and
MyText (of type Text).
After the first of these three lines executes, the value in property MyEncrypted is encrypted. After the second line, the value in property MyText matches the value of MyEncrypted; no encryption or decryption takes place. After the third line, MyEncrypted holds the encrypted value from "Rosebud"; encryption is implicit.
To use a TextEncrypted property as a selection
criteria on the Content tab of a
list view or summary view rule:
TextEncrypted property a database
column.
Is Equal To or Is Not
Equal To for the comparisons.
![]() The rule forms accept
comparisons other than
The rule forms accept
comparisons other than Is Equal To or Is Not
Equal To, but results are unpredictable.
If an external system calls a service and sends to Process
Commander a (clear text) value for a field that is mapped to a
TextEncrypted property, the value becomes
encrypted as soon as it reaches the clipboard.
Responses to service calls and connector requests normally send only the encrypted value. Your application can call the standard function @decryptPropertyValue() to send the decrypted, clear text value, but only in a context when the access when rule is true.
Don't send an encrypted property value to an external system that expects the clear-text value.
On the Clipboard tool display, the value of a
TextEncrypted property is blank.
Except as described here, Process Commander treats the value
of a TextEncrypted property similar to a
Text property. Your application can place dates or
numbers in the value, but no validation occurs.
|
|
exposed column, type |
|
|
About Access When rules |