In a time when data breaches make common headlines, building secure enterprise applications is non-negotiable. Securing an application isn’t just about ticking boxes, it’s about protecting the people who use it. When an app is secure, users can trust that their data is safe and businesses can operate with confidence. Security is a responsibility that starts from day one and continues throughout the app’s lifecycle.
Pega GenAI Blueprint™ addresses this need head-on by generating applications that are Secure By Default. One standout feature of this approach is that none of the Personas in the application representing various user roles have access to Cases or Data when the application is created. This blog dives into how this design strengthens security and why it matters for your organization.
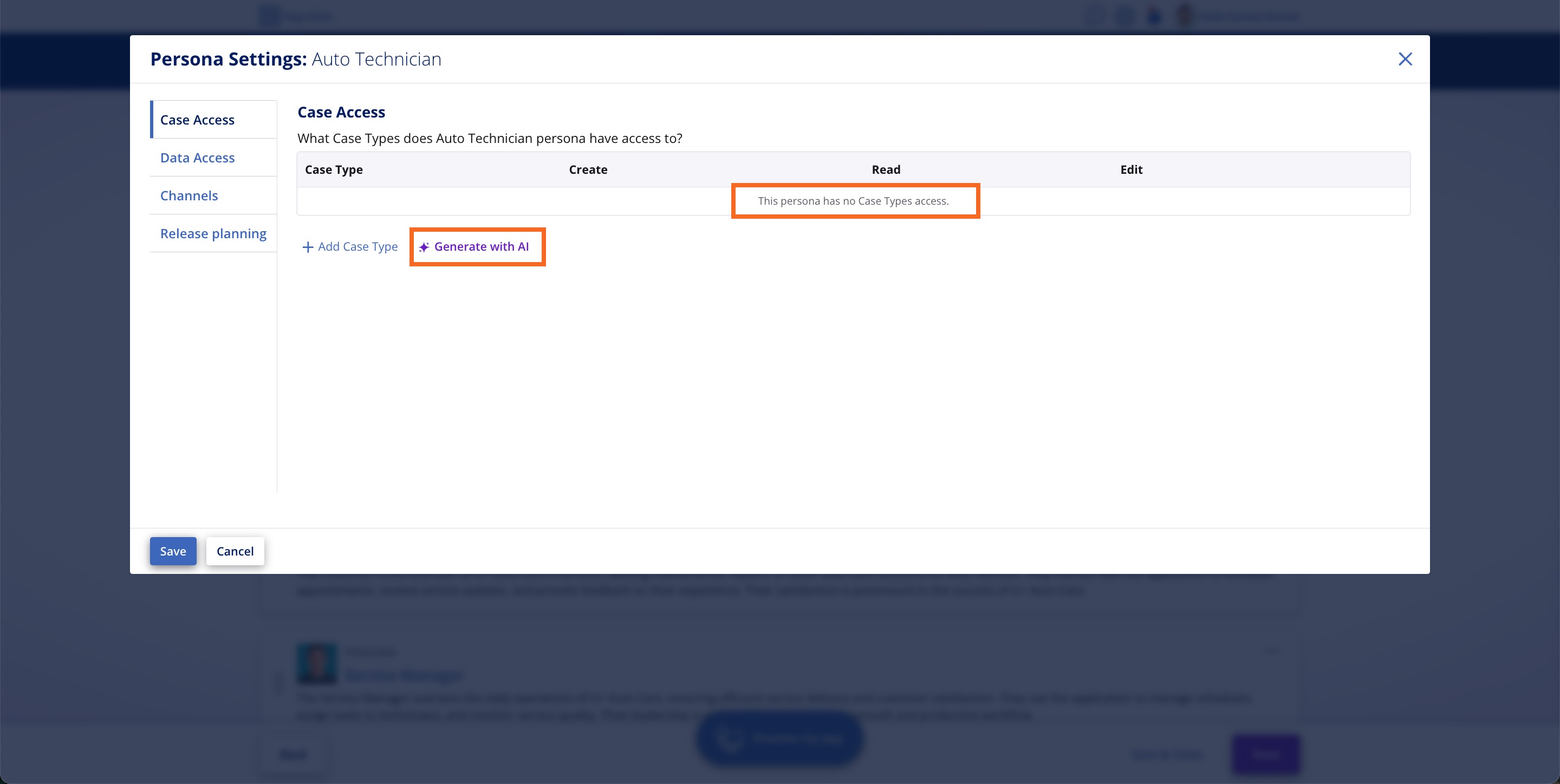
Generated application with zero default access
When Pega GenAI Blueprint generates an application, it starts with a locked-down foundation. Cases (the workflows that drive your business processes), and Data Objects (the information fuelling those workflows), are inaccessible to all the Personas by default. Whether it’s a Customer Service Rep, a Manager, or an Administrator, no one can view or modify anything until permissions are explicitly assigned. This isn’t an oversight, it’s a deliberate security choice.
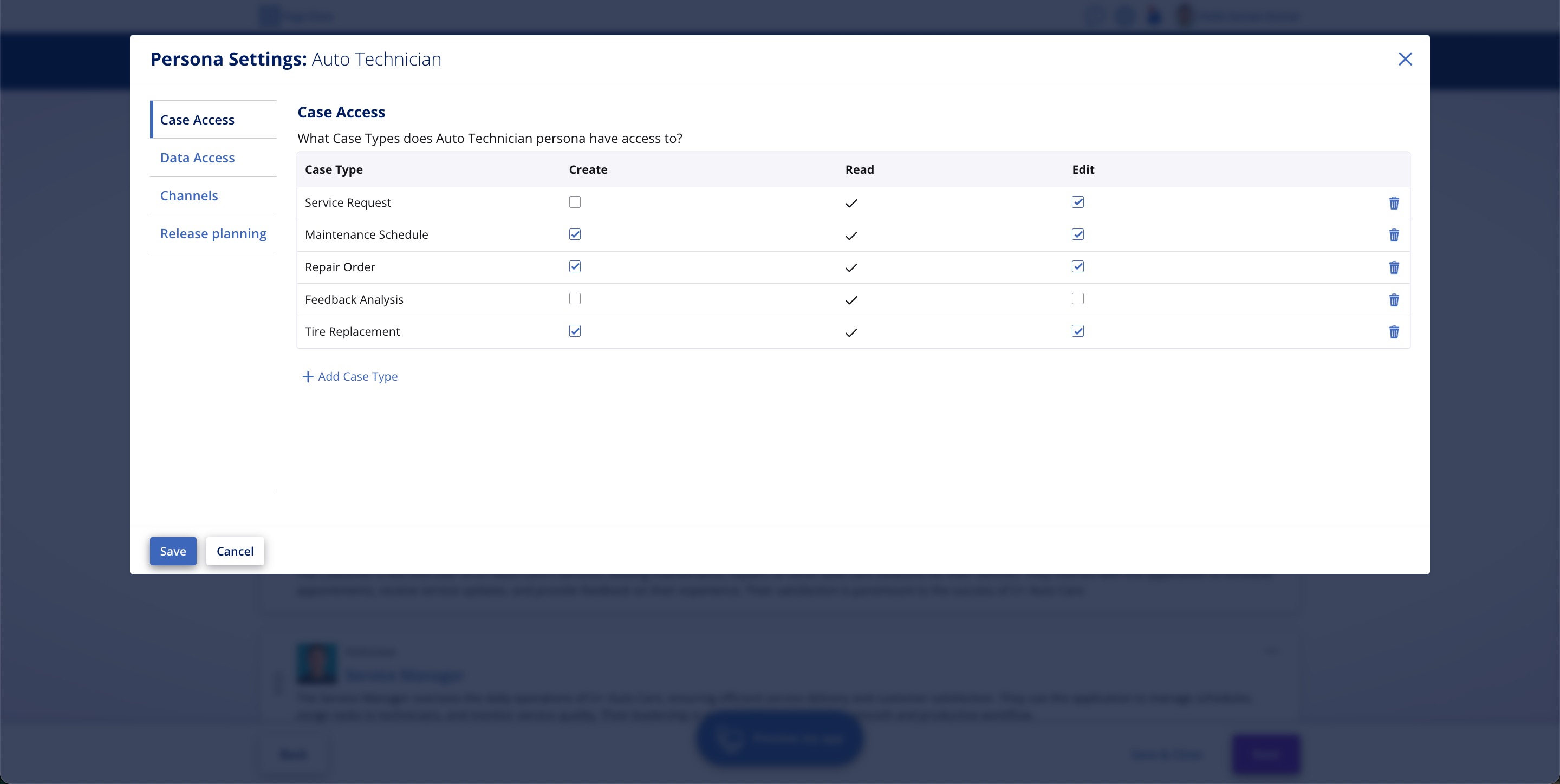
By ensuring that the generated application begins with no access granted, Pega eliminates the risk of unintended exposure right from the start. Instead, it is you who must provide access to Cases and Data Objects for each of the Personas, after performing careful due diligence. Of course, you can also use Pega GenAI™ to speed this up, because Blueprint gives you the option to let Pega GenAI generate access permissions for each Case and Data Object. Pega GenAI analyses the Persona description and all the Cases and Data Objects in your application, and based on its analysis, proposes what all Cases and Data Objects each Persona should have access to. Plus, you can always adjust this based on your needs.
Why this matters?
This zero-default access aligns with the principle of least privilege, a foundation of modern security practices. The principle of least privilege means giving users and systems only the access they absolutely need. It reduces the risk of accidental or intentional misuse by limiting exposure. By keeping access tightly controlled, organizations can better protect sensitive data and minimize the impact of potential breaches. In a typical application, broad, pre-assignedpermissions might accidentally enable users to see sensitive data or perform critical workflows. With Blueprint, the generated application avoids this pitfall entirely. Organizations can define exactly who needs access to what, tailoring permissions to specific roles and responsibilities. This results in a secure application in which sensitive Cases and Data Objects remain protected until you intentionally open them up.
Key security features of Blueprint
- No Access by Default: Every persona in the generated application, whether it’s a Customer Service Rep, a Manager, or an Administrator, starts with zero access to Cases and Data Objects. This ensures that no one slips through the cracks.
- Pega GenAI assistance on Access configuration: Get assistance from Pega GenAI to define access to different Cases and Data Objects for each of your Personas. You can review and update the access permissions suggested by Pega GenAI to meet your business needs.
- Protection from Day One: When the Blueprint is imported and the new application is created, its Cases and Data Objects are protected with the already-configured access permissions, removing any chances of access-related vulnerabilities.
Benefits of a Secure-by-Default application
This approach delivers tangible advantages:
- Lower Risk: With no default access, the generated application minimizes the chance of unauthorized users viewing or altering Cases and data.
- Compliance Made Easier: Starting with a secure baseline helps organizations meet strict regulations by ensuring that sensitive information isn’t exposed unintentionally.
- Simplified Security Management: Administrators can focus on granting access when needed, rather than revoking unwanted permissions, streamlining the process.
Security built into every application
Pega GenAI Blueprint’s secure-by-default approach confirms that all applications start with a resilient security framework, offering a strong shield against vulnerabilities. This strategy enforces strict access controls from the beginning, ensuring long-term compliance and trust, which in turn enables organisations to secure their workflows and data with certainty and confidence.
Related Resources
- Pega GenAI Blueprint™
- How Pega GenAI Blueprint protects your confidential data
- Security features in Pega Platform
Don't Forget
JOIN THE CONVERSATION on Support Center


