Process mining is an innovative analytical technique that enables organizations to gain deep insights into their operational processes. By analyzing event logs from various systems, businesses can visualize, understand, and optimize their workflows. However, prioritizing the right processes or cases for process mining is crucial for quickly maximizing the value derived from this technique.
This post explores an easy-to-apply framework for process selection, which categorizes tasks based on their business value and assumed inefficiency in detail and provides guidance on how to apply the framework effectively.
I will additionally provides some example actions plans that illustrate how to make use of machine learning (such as Process AI), natural language processing (NLP), and performance accelerators such as Pega GenAI™ to improve processes and cases.
Understanding the Framework
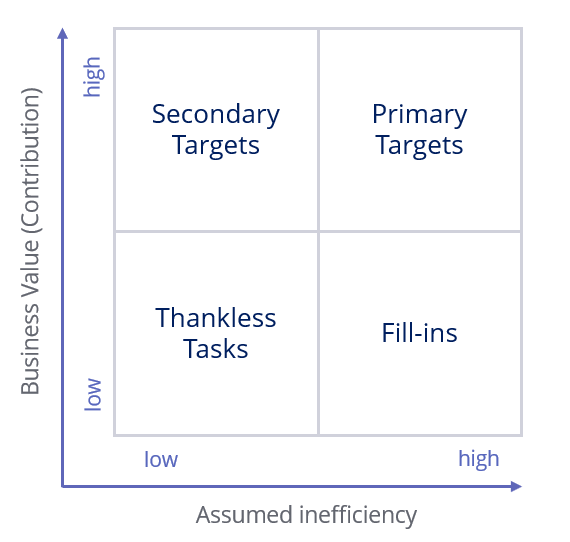
The framework categorizes processes into four quadrants based on two axes: Business Value (contribution), and Assumed Inefficiency. The four quadrants are:
- Primary Targets
- Secondary Targets
- Fill-ins
- Thankless Tasks
Each quadrant represents a distinct type of task with specific characteristics and strategic implications:
Primary Targets
Characteristics:
- High Business Value
- High Assumed Inefficiency
Strategic implications: Primary targets are the most critical tasks in process mining. These tasks have a high impact on the business's overall performance and are assumed to be inefficient. Focusing on these tasks can yield significant insights and improvements, leading to major operational enhancements.
Examples:
- Core business processes like order-to-cash or procure-to-pay.
- High-volume customer service operations with potential inefficiencies.
- Key production processes in manufacturing with suspected bottlenecks.
Example action plan:
- Identify high-impact processes: Look for processes that are central to your business operations and have a direct impact on revenue or customer satisfaction.
- Analyze event logs: Collect and analyze event logs to pinpoint inefficiencies and deviations from the ideal process flow.
- Implement AI-driven improvements: Use Process AI to predict and mitigate inefficiencies. Apply NLP to automate data extraction and analysis from unstructured sources, such as customer feedback and service logs. Utilize performance accelerators such as Pega GenAI to create intelligent assistants that guide employees through complex tasks, reducing errors and improving efficiency.
Secondary Targets
Characteristics:
- High Business Value
- Low Assumed Inefficiency
Strategic implications: Secondary targets are also important to the business but are perceived to be relatively efficient. While these tasks may not offer the same level of improvement potential as primary targets, analyzing them can still provide valuable insights and help to fine-tune operations.
Examples:
- Established customer onboarding processes.
- Routine financial reporting tasks.
- Standardized supply chain operations.
Example action plan:
- Use process mining for validation: Use process mining to validate assumptions of efficiency and identify any emerging inefficiencies. Make sure this is not a Primary Target!
- Conduct periodic reviews: Regularly review these processes to ensure that they remain efficient and effective. Use BPMN models and Dashboards to highlight when process runs falloutside of your accepted parameters.
- Implement AI-driven improvements: Should you find deviations from the accepted path, use Process AI to predict and mitigate inefficiencies. Apply NLP to automate data extraction and analysis from unstructured sources, such ascustomer feedback and service logs. Utilize performance accelerators such as Pega GenAI to create intelligent assistants that guide employees through complex tasks, reducing errors and improving efficiency.
Fill-ins
Characteristics:
- Lower Business Value
- High Assumed Inefficiency
Strategic implications: Fill-ins are lower-priority tasks with high inefficiency. These tasks are not urgent or critical and can be worked on during downtime or less busy periods. While they do not contribute significantly to business value, optimizing them can free up resources for more important activities.
Examples:
- Routine administrative tasks.
- Minor maintenance activities.
- Non-critical reporting.
Example action plan:
- Schedule during downtime: Assign these tasks during periods of low activity to avoid disruption to critical operations.
- Analyze with Pega Task Mining: Capture event logs from your employees’ desktops to see where Intelligent automation could be leveraged to free up time for more value adding tasks.
- Simplify and automate: Use Intelligent Automation, such as attended desktop robotics to simplify or automate these tasks, reducing their inefficiency.
- Monitor periodically with Pega Task Mining: Periodically review these processes and identify opportunities for further automation and efficiency improvements.
Thankless Tasks
Characteristics:
- Low Business Value
- Low Assumed Inefficiency
Strategic implications: Thankless tasks rank at the bottom of the to-do list. They have low business value and low inefficiency, meaning there is minimal benefit in investing resources to optimize them. These tasks should be deprioritized in the process mining efforts.
Examples:
- Routine data entry with no strategic value.
- Basic housekeeping tasks.
- Low-impact administrative activities.
Example action plan:
- Minimal attention: Spend as little time and resources on these tasks as possible.
- Outsource or automate: Consider outsourcing or using AI-driven automation to handle these tasks, minimizing their impact on internal resources. Employ RPA and NLP for simple automation.
- Focus on high-value tasks: Redirect efforts towards more valuable tasks that offer better returns on investment.
Using the Framework
To effectively apply this framework, organizations should follow these steps:
- Map out all processes: Use or create a comprehensive map of all business processes at a detailed level (for example, Level 3) and categorize them into the four quadrants based on their business value and assumed inefficiency.
- Finding Process Maps:
- Enterprise Architecture (EA) Tools: EA tools often contain detailed process maps.
- Business Process Management (BPM) Software: Look into your organization's BPM software, which likely has extensive process documentation.
- Internal Documentation: Check internal repositories, SharePoint sites, or document management systems.
- Consult Department Heads: Speak with department heads or process owners who have detailed knowledge and documentation of their respective processes.
- Level 3 Processes:
- Definition: Level 3 processes provide a detailed view of a business process, breaking down the high-level (Level 1) and mid-level (Level 2) processes into more granular steps.
- Example: For an Order-to-Cash process:
- Level 1: Order-to-Cash.
- Level 2: Order Management, Invoice Processing, Payment Collection.
- Level 3: Order Entry, Order Validation, Order Fulfillment, Invoicing, Payment Receipt, etc.
- Finding Process Maps:
- Prioritize tasks: Prioritize tasks according to their quadrant, focusing first on primary targets, followed by secondary targets, fill-ins, and finally, thankless tasks in the Process Mining backlog.
- Process and task mining: Use process mining tools to collect data from event logs and analyze the performance of prioritized tasks.
- Implement improvements: Based on the insights gained, implement process improvements.
- Review and adjust: Monitor the results and review the impact using process and task mining tools, and iterate as necessary, readjusting priorities in the backlog as needed.
Conclusion
Selecting the right process for process mining is critical to achieving significant operational improvements. By using the framework described above, organizations can strategically prioritize tasks based on their business value and assumed inefficiency. Focusing on primary and secondary targets will yield the most impactful results, while fill-ins and thankless tasks should be managed efficiently to free up resources. Implementing this structured approach ensures that process mining efforts are aligned with business goals, driving continuous improvement and sustained competitive advantage.
Related Resources
Don't Forget
- JOIN THE CONVERSATION on Support Center
- FOLLOW @PegaDeveloper on Twitter

